In a recent membership meeting, member institutions of MDREN, Maryland’s State-Wide Research and Education Network, identified Distributed Denial of Service (DDoS) Mitigation as one of the networks strengths. According to Norwin Malmberg, chief network technology officer, “The fast, 30-second time to detect and mitigate is a substantial factor in preventing institutions from even noticing that an attack took place.”
According to Michael Gemeny, senior network engineer, “The system has been fully automatic for over two years now, and has successfully identified and mitigated over 75 DDoS attacks. By the time we see the page, the mitigation has already kicked in.”
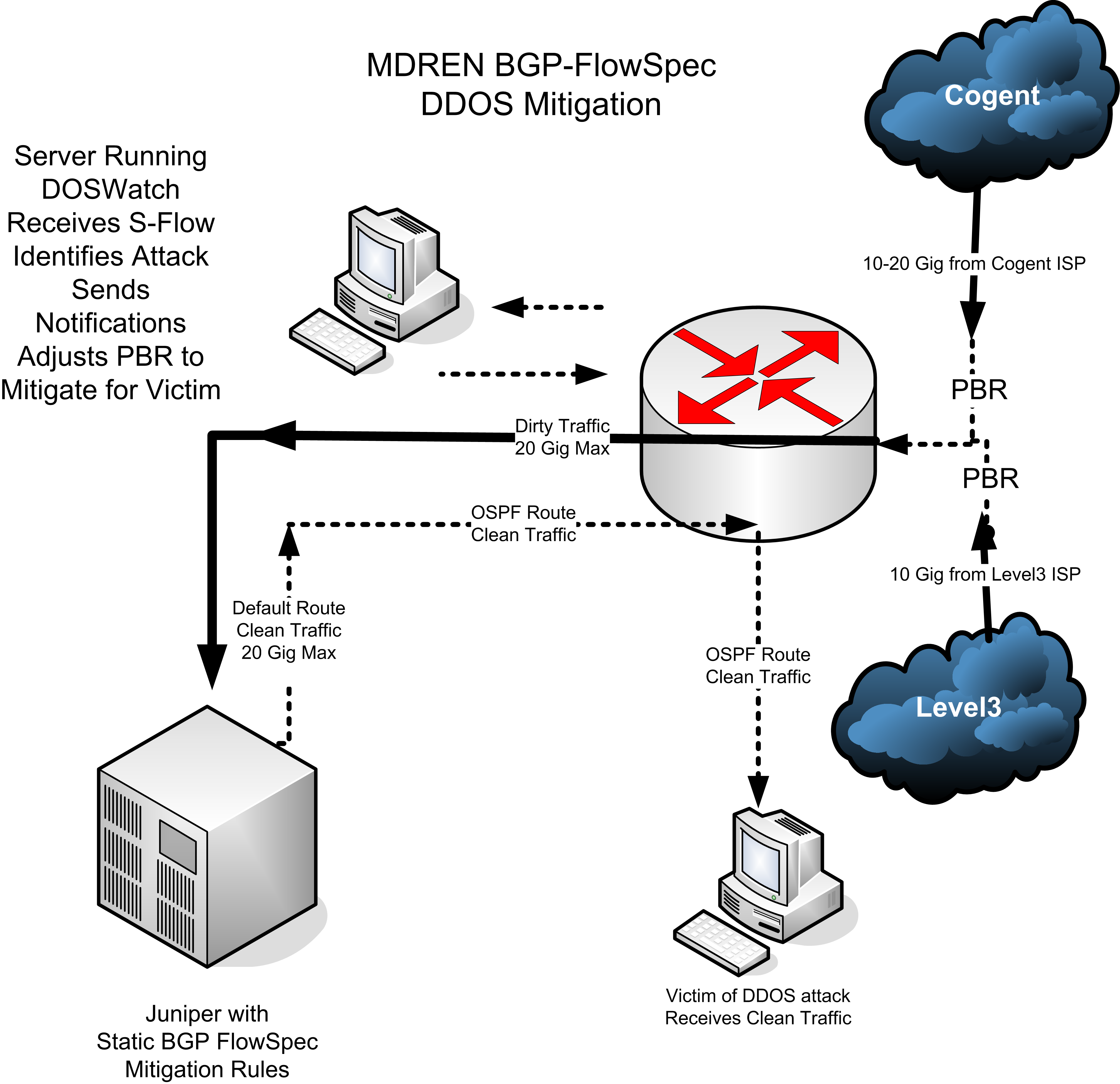
The scrubbing engines are based on Juniper routers running a static BGP-Flowspec rule set which rate limits every known DDoS amplification vector. This effectively discards the attack traffic while passing the legitimate traffic to the IP address under attack.
“We originally were using an old Juniper M20 recovered from the scrap pile as our scrubber, but recently we upgraded to a pair of Juniper MX104 routers. This allows us 20 to 40 Gig of dirty traffic scrubbing capacity on net,” Gemeny said. While the original configuration was based on equipment which was essentially free, the upgraded configuration was a one-time investment of $56,000.
The core routers (facing upstream ISPs) are Brocade routers, and do not support BGP-Flowspec, so the Juniper routers, used as scrubbers, are applied as a companion “appliance” to the ingress routers. When a DDoS attack is detected, Policy Based Routing (PBR) in the Brocades are adjusted, routing the victim IPs ingress traffic through the scrubber. Once scrubbed, the clean traffic is returned to the same core router. However, this time it is not coming in from an ISP connection. As such, it is not subject to the PBR and is routed to its destination with normal Open Shortest Path First (OSPF) routes.
The DDoS detection software was written in house and is a mixture of C and Perl running on a standard UNIX NOC server. This software monitors S-Flow data from the ingress routers, and dispatches shell scripts to adjust the PBRs and send pages when attacks are identified.
“It takes 5 seconds to identify an attack, 5 more seconds to quantify the attack, then 10 seconds to adjust the PBRs, and an additional 10 seconds for the routers to actually do what they have been told to do. That adds up to 30 seconds,” said Gemeny.
Malmberg added that, “We do subscribe to Internet2’s ZenEdge DDoS mitigation service for peace of mind, but we’ve never had to use it. The on-net mitigation is faster and only affects the single IP address under attack, which reduces the chance of inadvertent side effects. The potential magnitudes of DDoS attacks seem to be unbounded, so it’s nice to have yet another option besides just a ‘Black Hole’.”